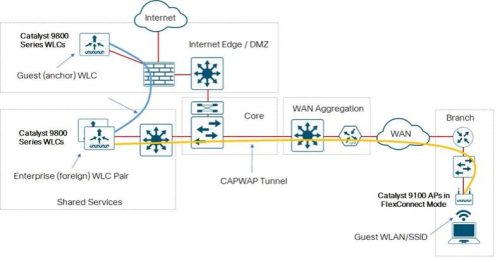
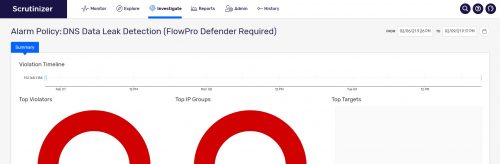
Machine learning is driving advances in NDR (network detection and response) and is the future of network security. Learn how Scrutinizer by Plixer uses NDR to protect against the unpredictable.
Tell us what you want to achieve and we’ll get in touch…