
“Based on your experience with our products and services, how likely are you to recommend Plixer to your colleagues? 10 – based on my research no other platform offers what Plixer does.” – Senior Network Engineer at a national telecoms operator on 4th May 2021.
About Plixer – network monitoring for security and performance
Plixer was founded in 1999 by two ex-employees of Cabletron Systems who left to become independent consultants. While consulting they used a number of different tools to monitor network traffic for their clients. In true entrepreneurial style they decided there was an opportunity to build a tool of their own that would do a much better job. Scrutinizer, their NetFlow collector and analyser, soon became the market leader.
The success of Scrutinizer was followed by FlowPro, the flow generator with DNS monitoring capabilities, and Replicator, for aggregation, replication and distribution of flows.
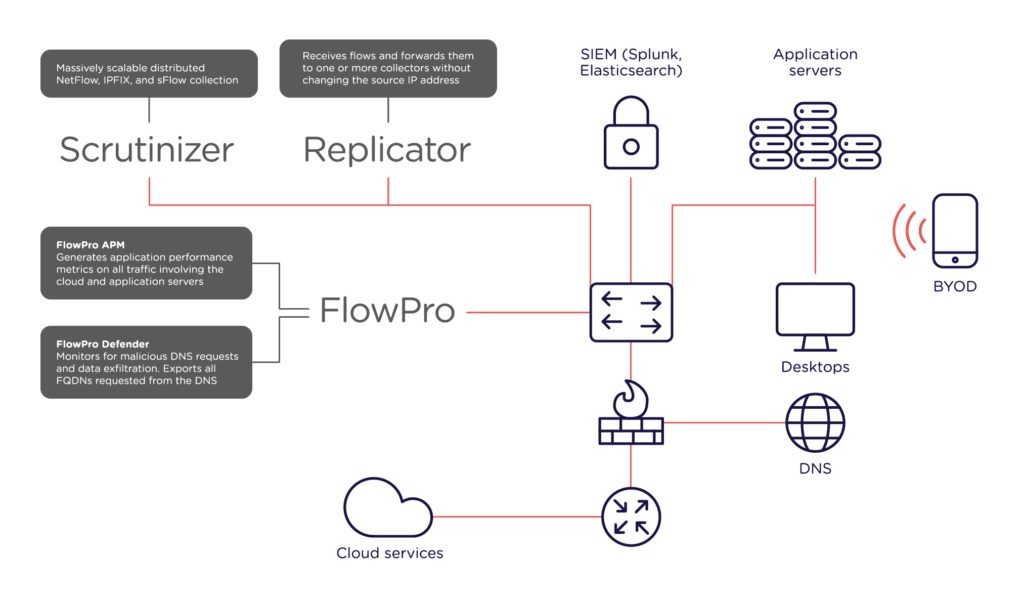
All these years later, Plixer are still entirely focused on providing network visibility through the collection and analysis of network-related metadata. Everything they do helps network performance and security teams respond to incidents with certainty, and to proactively detect issues before they begin to affect user experience or compromise the protection of valuable digital assets.
In August 2018 Plixer were acquired by Battery Ventures, an international technology-focused investment firm. In addition to appointing a highly experienced management team, they have been investing heavily in product development.
Here’s a short video about Plixer:

Find out more about the Plixer products available through Info stor:




