The release of TLS 1.3 marks a turn of the tide in the cybersecurity theatre. For the past decade, network managers have become embattled by the threat of cyberattacks. The innovation of malicious actors forced a strategy of firefighting: network managers scrambled from incident to incident, retroactively addressing vulnerabilities and deriving whatever insights were available.
Pre-emptive action depends upon data, and the ability to detect vulnerabilities or patterns before an attack occurs. Without this, there is only triage: dealing with attacks after they’ve occurred and mitigating the damage inflicted. The inefficiency and ineffectiveness of this strategy increase as networks grow. Secure scaling of a network’s capacity and performance is only possible through data-driven, proactive strategies that not only incorporate the latest encryption standards, but also use the tools necessary to monitor and analyse encrypted traffic.
How big is the threat?
Few network managers require statistics to be convinced of the threat of cyberthreats, but many still underestimate the scale of the problem. Attacks we hear about are abstract and distant; they happen to another, not to us. A 2019 IBM report found that the average cost of a data breach is $3.92m, each with an average loss of 25,575 records. In reality, there is no way to quantify the potential impact of a data breach. Some effects are immediate – such as the need to rectify any vulnerabilities, recover records, and inform customers – and some take longer to materialise and impact bottom lines, such as loss of client or customer confidence.
Encryption and TLS 1.3
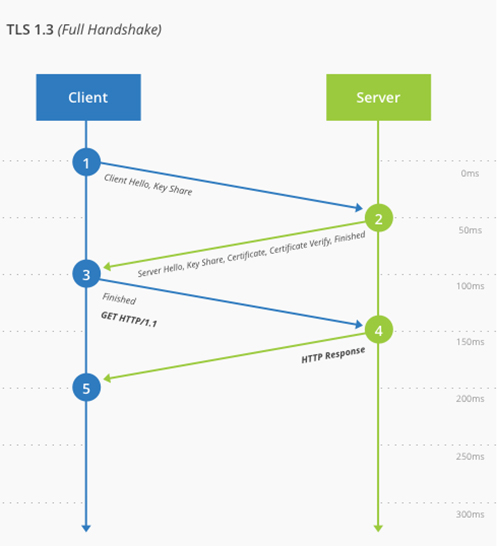
For the uninitiated, TLS refers to Transport Layer Security, the successor to SSL (Secure Sockets Layer), and is a protocol used to ensure secure communication between servers by encrypting the data transmitted. It leads the fight against cyberthreats by ensuring the data transmitted, even if somehow compromised or retrieved, cannot be unravelled to expose its contents. TLS 1.3, meanwhile, provides the same benefits but at greater speed and efficiency: the balance between performance and security is a continuous tug-of-war, and TLS 1.3 makes it easier to find a secure and scalable middle ground.
It achieves this through features such as TLS false start – which you can read about here – and Zero Round Trip Time (0-RTT): a method of client-server communication that means only one round-trip is necessary, effectively cutting encryption latency in half.
Understanding and identifying encrypted cyberthreats
So, does encryption solve the threat of cyberattacks? Well, no. As we’ve already mentioned, attackers are more than capable of innovation. Now, network managers also have to contend with cyberthreats hidden in encrypted traffic. Updates to TLS – and, specifically, TLS 1.3 – help to mitigate these dangers, but the onus of detection and elimination is placed on network managers.
A study from A10 Networks found that 41% of cyberattacks used encryption to evade detection. This is the double-edged sword of encryption: it helps to obfuscate and hide the transmission of sensitive data, but also offers cover to cyberattacks. In this nebulous slipstream of data, a would-be cybercriminal can operate undetected.
Network managers are only now awakening to the need for better tools to monitor, detect and identify encrypted cyberthreats. Luckily, solutions already exist. Ixia, Plixer and Endace each offer easily deployable tools to help identify, analyse and mitigate encrypted cyberthreats.
Each gives you better control over your network, providing the real-time insight necessary to detect patterns and intrusions within encrypted traffic, and the tools to access packet capture data for significantly improved analysis. Matching innovation with innovation, these solutions help you stay ahead. To discuss which is best suited to your specific needs, or to arrange a demo, contact us today.