When we live through data, data theft becomes the greatest threat. For corporates – the stewards of vast quantities of data – this threat is amplified, their duty to safeguard anchored by the now high-profile consequences of failing to do so. According to a study by McAfee, almost half of IT professionals have experienced at least one data breach in their careers. With the surging frequency of data breaches, from the minor to the major, most professionals will develop a portfolio of experiences over the next two decades.
But it isn’t a one-way tide. To counter new attack vectors only requires a more proactive approach and a more intimate awareness of how to identify and combat new threats. This includes adopting a set of best practice procedures, training those responsible for network security, and improved monitoring of traffic to identify threats in real-time. That’s where FlowPro comes in, but first, let’s speak to the other steps: what to look for and best practice for prevention.
How to spot data theft vectors
Prevention nearly always begins with understanding. To ascertain how vulnerable a network is to data theft, you have to know what you’re looking for.
First is the biggest culprit: blind spots. It is easy for a corporate network to end up with blind spots. These can include vulnerabilities created by remote employees, branch offices, retail locations, or other unmonitored backdoors into corporate networks. Left unchecked, malicious actors will use these backdoors as the first rung in a ladder – as staging points to gain access into more critical parts of the network. A corporate firewall is an obstacle; an employee liberal with their laptop use and website browsing less so.

This is where best practice policies make a difference. As companies grow, not only does the size and capability of the network need to change, but the logic governing its structure. Sensitive information should always be located on a part of the network not easily accessible to the majority of employees. Similarly, secure servers that store financial transactions or PoS systems should have restricted access, and for any access to be tracked. This, however, is part of the problem with access control; as the network grows, it becomes more convoluted and involved, and more difficult to track. Still, contemplation of the network structure and whether critical secures are appropriately segregated is an essential first step to preventing data theft, with additional policies building on top that foundation.
Other best practices for data loss prevention
Policies that enforce strict laptop use and remote employees to take security precautions – such as having a quality firewall installed and two-factor authentication on work devices – help prevent the majority of low-level threats.
But now what? You’ve done all you can to prepare your network and employees. The truth is that better procedures can only take you so far; it is monitoring and analytics that do the rest. Oversight of a network and how it’s interacted with and operated will provide a solid fortification against data theft. But insight – a clear picture of all network activity and traffic – can be used to create an alert system, for real-time response to threats before any data is lost.
This is essential because, as another McAfee report shows, only 61% of breaches are ever discovered. Undiscovered breaches are unreported. It means problems aren’t known and, consequently, there’s no visibility into the effectiveness of introduced procedures.
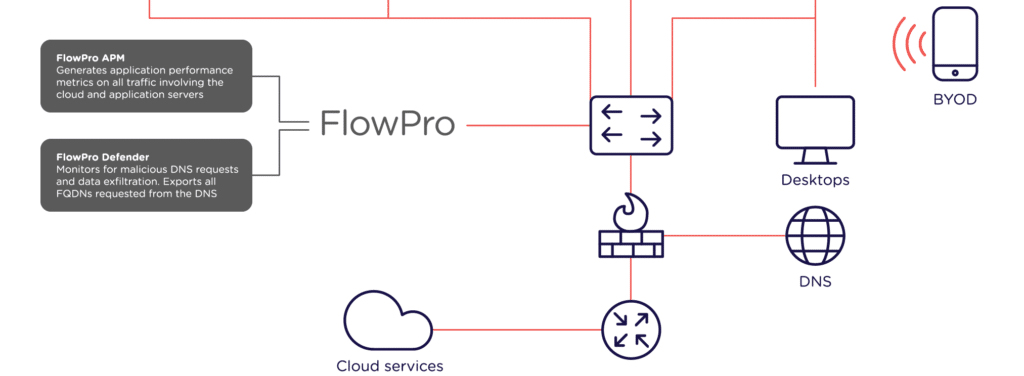
Introducing FlowPro
Monitoring DNS traffic is the key to preventing data theft. This becomes possible with FlowPro. With it, you can detect threats as they begin, including, for example, unauthorised credential use (it’ll even tell which credentials were used and when). Corporate network infrastructure is awash with rich network data. FlowPro uses this data to provide insight into what’s happening at any given time, as well as where and by which actor. As more traffic is encrypted, DNS traffic is becoming a more vital resource in identifying and combating data theft threats. It also provides visibility to network devices unable to generate metadata, or in cases where doing so would generate an unacceptable load on the device, as well as jitter and latency metadata – which are critical to monitoring voice and video traffic.
So, begin with policies and best practice procedures, but extend to more powerful solutions that offer the capability to unearth the activities of would-be intruders just as they’re getting started. For more information about FlowPro or preventing data thefts, contact us today, or get started by downloading a 30-day free trial.