In our last blog post, we talked about the importance of monitoring edge computing traffic. Edge computing is the deployment of network applications and devices nearer to your users, to maintain a geographically-agnostic network. Wherever your users connect from, they’ll receive the same network performance, speed and experience. Now, we’re going to talk about how to gate traffic and secure your network using inline security.
More complex networks require more comprehensive security solutions
To the end-user, the benefits of high security aren’t as readily apparent as speed or performance. But high security is what holds the user experience together. The consequences of allowing any point of security exposure to survive can be catastrophic, both to the user and your organisation’s brand. Edge computing, whilst essential for consistent service provision, creates new vulnerabilities and exposes networks to new attack vectors. These include an increase in the velocity and variety of cyberattacks, number of alerts, malware hidden in encrypted traffic and hard-to-detect breaches. Any of these will impact network performance. When stacked, however, these threats can significantly impact your organisation’s bottom line – or worse, jeopardise your organisation’s brand.
Like any defence, lines weaken as they extend – or, at least, this is true without sufficient preparation and the pre-emptive strategies. For networks, this means effective tools for monitoring and gating edge traffic with inline security solutions. The size of a network cannot be allowed to determine its security. Networks are growing every day and must reach disparately located users, from all corners of the world, securely.
Introducing inline security
Proactive defence is the answer. Inline security solutions help identify and resolve security threats of edge computing in real-time. Inline security solutions are most aptly compared to gateways. When done right, they provide a means to monitor all traffic that goes through a specific point in your network. If this point is near an edge computing network device, then you gain complete visibility of all traffic that comes from that point – no matter its location or distance from your core network infrastructure.
An effective inline security solution means more than adding a security appliance, however. Preventing the entrance of malicious traffic or detecting an intruder is just one part of an inline security solution. Inline security solution devices must be paired with complete data visibility, to derive rich context from data and better detect the how behind the what. If a malicious actor attempts to gain access through a network’s edge computing, understanding the intention is as important as detection – to know the tools used and whether any persisting vulnerabilities were exploited. Part of an inline security solution must include the ability to read and understand traffic.
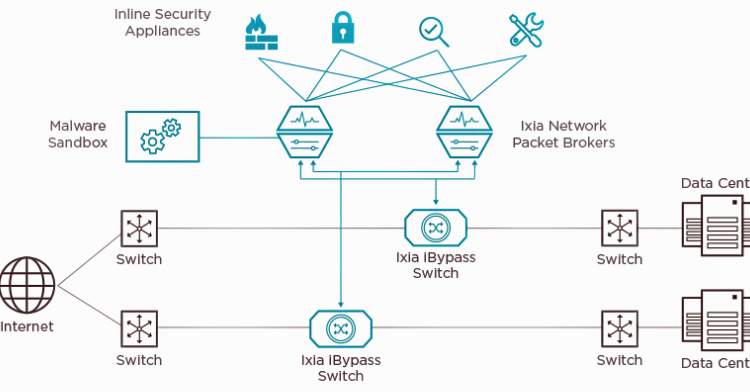
Build complete inline security solutions with Ixia’s network taps
This can be through the inclusion of an external bypass switch and a network packet broker (NPB), in addition to the security appliances. It can also include Ixia’s network taps: a cost-effective alternative to NPBs that allows network managers to aggregate and assess data, to maintain performance and security at scale. Network taps are an effective way to gain complete, 100% visibility into network traffic, and can be placed at any network location. Affordable and easily deployable, they can be spread across key access points to your network, including from and between edge computing, to ensure that you have insight into all traffic, and are able to immediately pinpoint the location of malicious behaviour.
The demand for edge computing is driven not just by its potential, but by its necessity as the requirements of networks evolve. Performance must be maintained alongside security, and vice versa. Network taps add no additional load to your network’s devices. Ixia’s network taps provide a way to build complete and comprehensive inline security solutions without the introduction of costly bottlenecks or points of failure.
For more information on implementing inline security solutions, and how to do so cost-effectively using Ixia’s network taps, contact us today.