It’s nothing new to say the threats networks face today are radically different to those faced a decade ago – and even a few years ago. Threats to network security will never cease to exist; they, like the solutions used to combat them, are continuously evolving, exploiting new vulnerabilities that arise from new integrations and data types.
Picture a network manager five years ago. Sat in a chair, multiple monitors spread across a utilitarian desktop, looking something like an overseer from any dystopian SciFi novel. Each monitor would display a dashboard, for anything from their antivirus and firewall to an email gateway or a status screen for switches and routers.
But the ability to look as though we’re in control doesn’t put us in control. Multiple dashboards were inefficient and, as the requirements of network managers and their networks changed, unsustainable. Now, we have more comprehensive, multi-purpose security solutions that combine different data from an increasingly diverse network environment, and provide new answers to mitigating network threats (identity and access management (IAM) solutions and cloud-based SD-WAN solutions, etc.)
The result is a densely populated network environment, which has created a couple of challenges. First is a challenge any network manager will recognise: data overload. We’re trafficking exponentially rising amounts of data that use different data types: logs, network traffic, IoT, threat intelligence, etc.
Second is the complication of attacks. Attacks, such as DDoS attacks, don’t happen within a single instant, but are often spread out over time. This is compounded by the first challenge. Network noise makes it more difficult to pin down specifics sets of data and determine root causes. Modern network attacks aren’t always known events. Knowing when an attack ended – and the resulting damage – is one thing. Knowing when it began is another.
Context is more important than ever. Understanding everything that happened around an event is critical to determining the event’s origin, and how to mitigate any future threat. A single indicator of compromise (IOC) cannot be relied upon.
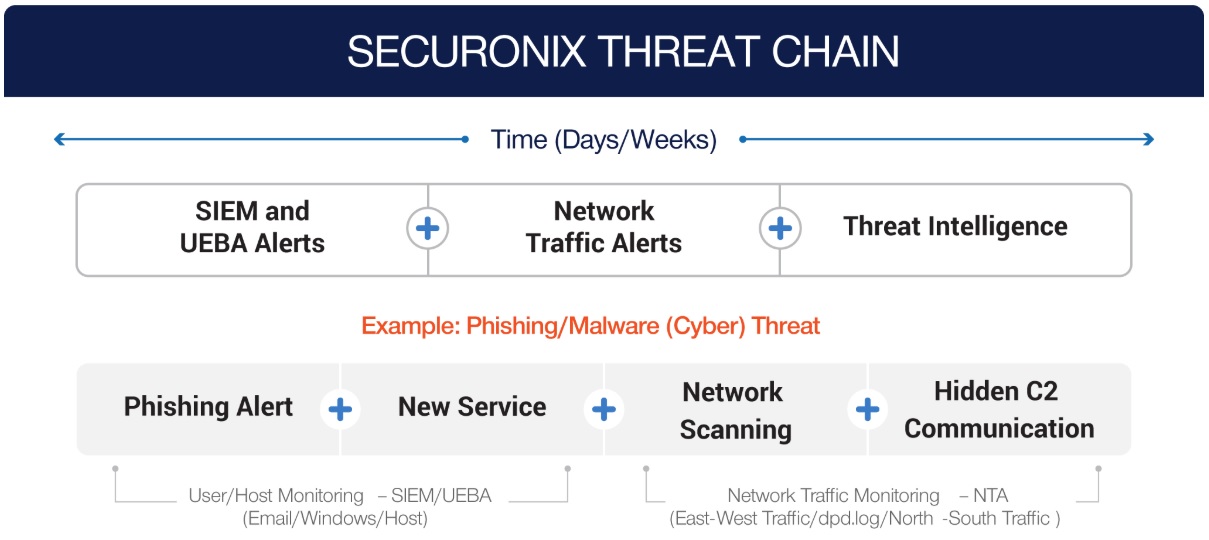
How threat chains help
Modern threats emerge through a pattern. To detect them, threat chains are necessary. Threat chains are a way to connect threats to individual entities (via username, IP address, login ID, etc.). Multiple threats caused by the same entity creates a pattern, so that a series of seemingly innocuous threats becomes an alert for a more significant threat.
This also opens up the door to machine learning and behavioural analytics. More advanced solutions, such as Securonix, are able to automatically detect patterns of behaviour that deviate from a ‘normal’ baseline. This is important today, but will become crucial in the coming years as network demand increases.
Securonix, risk modelling and tracking
Securonix makes it possible to do a lot more with a lot less: to combat diverse threats rising from disparate actors in a complex, data-heavy network. Its threat chain models are based on industry-standard threat modelling, including, among others, the MITRE ATT&CK framework and US-CERT Cybersecurity Framework.
Its analytics engine can identify relationships across all assets linked to an entity, rather than individual identifiers specific to the solution’s application (firewalls tracking IP addresses, for example).
Effective combatting of threats begins with prioritisation. Threat chains allow you to see the greater significance of minor events, but risk modelling is still required to tackle threats efficiently. Securonix’s risk modelling elevates the risk associated with a specific threat chain, using both static scoring – scoring the threat chain from a single entity differently depending on other information associated with the entity, such as their criminal history – and predictive exponential scoring: escalating the importance of a threat in accordance with what the entity may do, indicated by the threat chain’s development.
Modern threats unravel as an avalanche: minor threats combined tell the story of a greater threat to come. Securonix helps you better combat multi-tiered threats through the automatic identification (configurable to a baseline), analysis and modelling of threat chains. To learn more about threat chains or the value of Securonix to your network, contact us today.