Nothing better exposes the limitations of popular services as news-breaking breaches. News of the Capital One data breach – in which details of 100 million peoples’ accounts were leaked – has damaged enterprise confidence in AWS at a critical time, and once more brought into question the security of cloud-based infrastructure as an all-in-one computing solution.
Large scale data breaches are not uncommon, but their frequency doesn’t detract from the danger posed. The Capital One breach comes at a time in which the decade-old reticence towards cloud-based services is cooling, with more companies opening up to cloud-based infrastructure. Recently, Amazon has been in the process of coaxing larger organizations – including banks – into using AWS, with the basic promise of lower cost, greater efficiency, and equal security.
Security Is About More Than The Physical
AWS is a global infrastructure spread across many physical locations. These locations, which contain the physical servers that host AWS, have numerous security guarantees in place to prevent outside tampering. They’re ironclad, locked away, secure – and prioritize hardware security above all else.
The Capital One breach isn’t about the security of cloud-based infrastructure as much it’s about the security of AWS as an end-to-end service: one that prioritises security of hardware over security of software, and fails to provide security between applications sharing the same cloud environment. In 2019, would-be hackers aren’t climbing into server fortresses clad in black, but through any available attack vector, including between cloud-based applications.
In Capital One’s case, there was no hack; the data breach was carried out by a former Amazon employee. Nevertheless, it’s highlighted the weak protections in place between applications within the same cloud environments, and the date they store. According to an FBI report, the breach was possible because of a firewall misconfiguration, which meant that the ex-employee was able to access customer data by first accessing Capital One’s web application.
But cloud-based infrastructure is the future, even if it requires more than what AWS is currently willing – or able – to provide. It requires security that looks beyond the physical, to that which exists between applications. The Capital One breach exposes the danger of this attack vector, and the need for the solutions to counter it.
Radware
Radware offers a number of products that protect AWS assets from different points-of-access, both external – from outside the native cloud environment – and internal, between different cloud-based applications and work groups. Their Cloud Protection Service, for example, provides both overall security for cloud infrastructure, but also protects individual cloud workloads against cloud-native attack vectors.
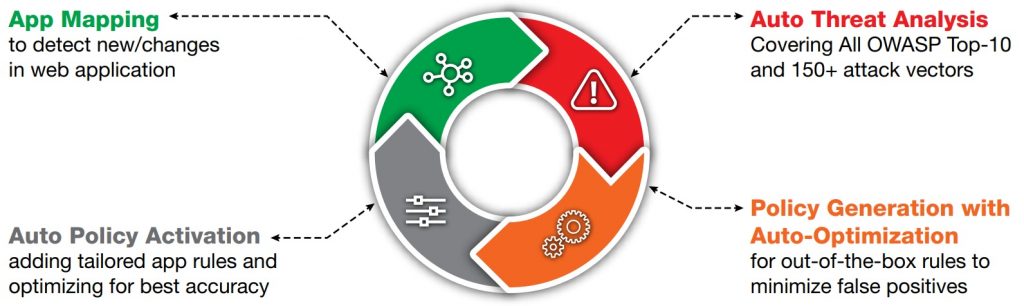
An overview of AppWall by Radware’s machine-learning capabilities
If there’s a reality that the Capital One breach underscores, it’s that the security of cloud-based applications isn’t taken as seriously as on-premise applications that run behind dedicated hardware firewalls.
AWS is popular for a reason; it’s the most capable, comprehensive cloud-based computing infrastructure available. But it can’t be relied upon for complete end-to-end security. Other solutions that ensure adequate protection between applications are necessary. Radware’s AppWall, a Web Application Firewall (WAF), combines positive and negative security models to provide complete protection against web application attacks. It creates and maintains security policies in real-time for wide security coverage, with the lowest false positives and minimal operational resource requirement.
If you’d like to learn about integrating Radware products into your cloud-based environment, contact us today. We’ll talk you through the security advantages, and help you create a more complete, secure cloud-based environment.


